Terraform tainted so must be replaced. This imperative introduces the concept of resource tainting in Terraform, emphasizing its significance and the consequences of tainted resources. It explores the scenarios that lead to tainting, highlighting the importance of understanding and addressing this issue effectively.
The subsequent paragraphs delve into the various replacement strategies for tainted resources, comparing their advantages and disadvantages. A step-by-step guide is provided for implementing each strategy, ensuring a practical understanding of the replacement process. Additionally, best practices for preventing resource tainting are discussed, emphasizing the role of version control and testing in minimizing the risk of tainting.
Terraform Taint Analysis
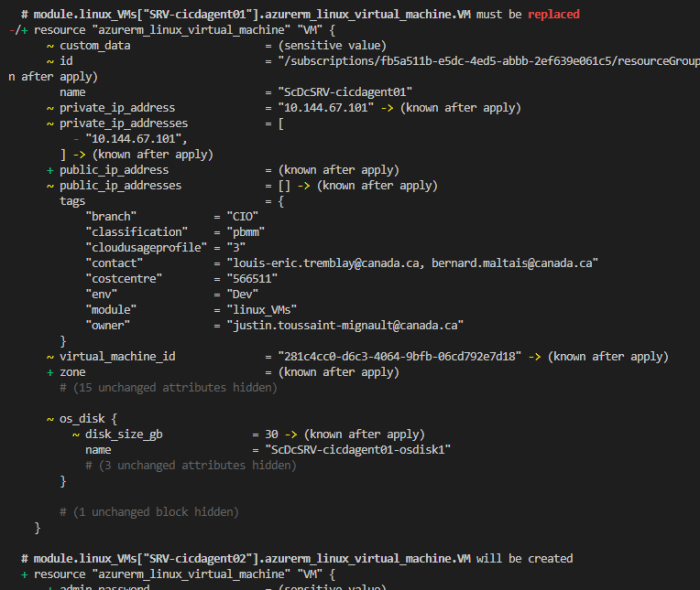
Terraform taint is a state that indicates a resource has been modified outside of Terraform’s control. This can happen due to manual changes, external tools, or API calls. Tainted resources are marked as invalid and cannot be managed by Terraform until the taint is removed.
The consequences of having a tainted resource can be severe. Terraform will not be able to make changes to the resource, which can lead to inconsistencies between the desired state and the actual state of the infrastructure. Additionally, tainted resources can prevent Terraform from detecting and fixing other issues in the infrastructure.
Examples of Scenarios that Can Lead to Resource Tainting
- Manual changes made to resources outside of Terraform, such as using the cloud provider’s console or API.
- External tools or scripts that modify resources without going through Terraform.
- API calls made to the cloud provider that are not managed by Terraform.
Replacement Strategies for Tainted Resources
There are several methods for replacing tainted resources in Terraform. The choice of method depends on the specific situation and the desired outcome.
Recreate the Resource
The simplest method is to recreate the resource. This will create a new resource with the same configuration as the tainted resource. However, this method will also destroy any data or state associated with the tainted resource.
Import the Resource
Another option is to import the resource into Terraform. This will add the existing resource to Terraform’s state without modifying it. However, this method can be risky if the resource has been modified outside of Terraform, as it may lead to inconsistencies between the desired state and the actual state of the infrastructure.
Use the “ignore_taint” Directive
The “ignore_taint” directive can be used to tell Terraform to ignore the taint on a resource. This can be useful if the taint is not relevant to the desired state of the infrastructure or if the resource cannot be recreated or imported.
Best Practices for Preventing Resource Tainting
There are several best practices that can help prevent resource tainting.
- Use version control for all Terraform configurations.
- Test Terraform configurations thoroughly before applying them.
- Use Terraform’s locking mechanism to prevent concurrent modifications to resources.
- Avoid making manual changes to resources outside of Terraform.
- Use external tools and scripts that are compatible with Terraform.
Advanced Techniques for Taint Management: Terraform Tainted So Must Be Replaced
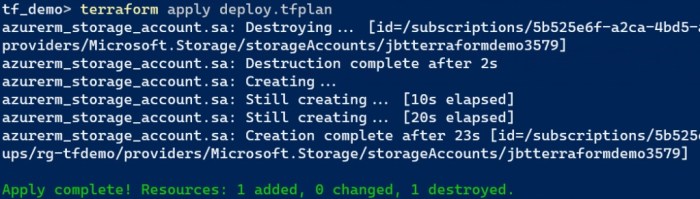
Terraform provides several advanced techniques for managing taint.
The “tainted” Attribute, Terraform tainted so must be replaced
The “tainted” attribute can be used to check if a resource is tainted. This can be useful for conditional resource management.
External Tools and Services
There are several external tools and services that can help with taint management. These tools can provide additional insights into tainted resources and help automate the process of replacing them.
Answers to Common Questions
What is resource tainting in Terraform?
Resource tainting occurs when a Terraform resource is marked as potentially compromised due to an error or unexpected behavior. It indicates that the resource may be unsafe or unreliable and should be replaced.
What are the consequences of having a tainted resource?
Tainted resources can lead to unexpected behavior, failed deployments, and security vulnerabilities. They should be replaced as soon as possible to maintain the integrity and reliability of the infrastructure.
How can I prevent resource tainting?
Best practices for preventing resource tainting include using version control, testing infrastructure changes, and avoiding untrusted sources for resource configuration.